
Computers and Technology, 26.12.2019 00:31 babygirlgabby2137
One of the earlier applications of cryptographic hash functions was the storage
of passwords for user authentication in computer systems. with this method, a
password is hashed after its input and is compared to the stored (hashed) reference
password. people realized early that it is sufficient to only store the hashed versions
of the passwords.
1. assume you are a hacker and you got access to the hashed password list. of
course, you would like to recover the passwords from the list in order to impersonate
some of the users. discuss which of the three attacks below allow this.
exactly describe the consequences of each of the attacks:
attack a: you can break the one-way property of h.
attack b: you can find second preimages for h.
attack c: you can find collisions for h.
2. why is this technique of storing hashed passwords often extended by the use
of a so-called salt? (a salt is a random value appended to the password before
hashing. together with the hash, the value of the salt is stored in the list of hashed
passwords.) are the attacks above affected by this technique?
3. is a hash function with an output length of 80 bit sufficient for this application?

Answers: 2
Another question on Computers and Technology

Computers and Technology, 22.06.2019 08:30
On the loan worksheet in cell c9 enter pmt function to calculate the monthly payment for the altamonte springs 2018 facilities loan. ensure that the function returns a positive value and set the reference to cells b5 and b6 as absolute references.
Answers: 2

Computers and Technology, 23.06.2019 20:30
1. for which of the following are you not required to signal beforehand? a. changing lanes b. speeding up c. stopping
Answers: 2

Computers and Technology, 24.06.2019 03:30
Auniform resource locator (url) is a formatted string of text that web browsers, email applications, and other software programs use to identify a particular resource on the internet. true false
Answers: 2

Computers and Technology, 24.06.2019 21:30
Suppose a router has built up the routing table shown in the table. subnet number 128.96.39.00 28.96.39.128 128.96.40.00 192.4.153.0 default) subnet mask 255.255.255.128 255.255.255.128 255.255.255.128 255.255.255.192 nexthop interface 0 interface 1 r2 r3 r4. the router can deliver packets directly over interfaces 0 and 1, or it can forward packets to routers r2, r3, or r4. describe what the router does with a packet addressed to each of the following destinations: (a) 128.96.39.10 (b) 128.96.40.12 (c) 128.96.40.151 (d) 192.4.153.17 (e) 192.4.153.90
Answers: 3
You know the right answer?
One of the earlier applications of cryptographic hash functions was the storage
of passwords f...
of passwords f...
Questions


French, 26.10.2020 20:40

Chemistry, 26.10.2020 20:40


Biology, 26.10.2020 20:40

Mathematics, 26.10.2020 20:40

History, 26.10.2020 20:40


Mathematics, 26.10.2020 20:40







Spanish, 26.10.2020 20:40



History, 26.10.2020 20:40

Mathematics, 26.10.2020 20:40

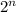 . It requires the attacker to have an idea about the kind of passwords that might be used and then brute force all of them to find string that has the same hash. Each try will have a chance of 1/
. It requires the attacker to have an idea about the kind of passwords that might be used and then brute force all of them to find string that has the same hash. Each try will have a chance of 1/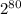 different hash values. This means there is at least one collision if
different hash values. This means there is at least one collision if 

