Computers and Technology, 02.03.2020 19:00 Porciabeauty4175
Suppose we are writing a program to calculate the gross pay of workers in a grocery store.
Which of the following Python programs will calculate each worker’s gross pay until the user does not answer ‘y’ to the question "Calculate another gross pay"?
A.
keep_going = input('Calculate another gross pay? [Enter y for yes] ')
while keep_going == 'y':
hours = float(input('How many hours did this worker work? '))
gross_pay = hours * 10
print('Gross pay:', gross_pay)
B.
keep_going = 'y'
if keep_going == 'y':
hours = float(input('How many hours did this worker work? '))
gross_pay = hours * 10
print('Gross pay:', gross_pay)
keep_going = input('Calculate another gross pay? [Enter y for yes] ')
C.
while keep_going == 'y':
hours = float(input('How many hours did this worker work? '))
gross_pay = hours * 10
print('Gross pay:', gross_pay)
keep_going = input('Calculate another gross pay? [Enter y for yes] ')
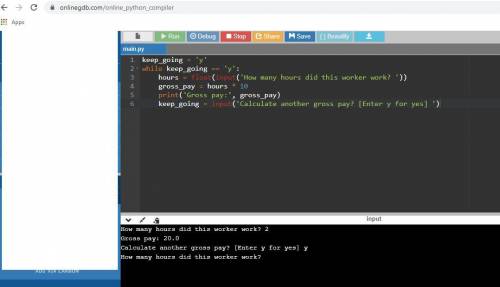
D.
keep_going = 'y'
while keep_going == 'y':
hours = float(input('How many hours did this worker work? '))
gross_pay = hours * 10
print('Gross pay:', gross_pay)
keep_going = input('Calculate another gross pay? [Enter y for yes] ')

Answers: 1
Another question on Computers and Technology

Computers and Technology, 22.06.2019 04:30
Dr. wisteria is a prominent chiropractor in the chicago area. she wants to provide a forum for her patients to discuss their health concerns and to seek and offer advice to other patients. which telecommunications tool is most appropriate for dr. wisteria's needs?
Answers: 3

Computers and Technology, 22.06.2019 17:30
1. before plugging in a new device to a computer you should unplug all other devices turn off the computer turn on the computer 2. many of the maintenance tools for a computer can be found in the control panel under administrative tools display personalization
Answers: 1

Computers and Technology, 23.06.2019 11:00
What are the possible consequences of computer hacking? what is computer piracy? describe some examples. what are the effects of computer piracy? what are the possible consequences of computer piracy? what is intentional virus setting? describe some examples. what are the effects of intentional virus setting? what are the possible consequences of intentional virus setting? what is invasion of privacy? describe some examples. what are the effects of invasion of privacy? what are the possible consequences of invasion of privacy? what is an acceptable use policy and what is the purpose of the acceptable use policy what is intellectual property and how can you use it?
Answers: 1

Computers and Technology, 23.06.2019 19:30
Of the following pieces of information in a document, for which would you most likely insert a mail merge field?
Answers: 3
You know the right answer?
Suppose we are writing a program to calculate the gross pay of workers in a grocery store.
Wh...
Wh...
Questions


Geography, 06.05.2020 06:41



Mathematics, 06.05.2020 06:41

History, 06.05.2020 06:41


English, 06.05.2020 06:41

History, 06.05.2020 06:41

Advanced Placement (AP), 06.05.2020 06:41


Biology, 06.05.2020 06:41








English, 06.05.2020 06:41