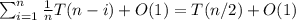Computers and Technology, 11.04.2020 04:46 bdog70
You are a police officer trying to crack a case. You want to check whether an important file is in the evidence room. Files have IDs that are positive integers and the evidence room contains n files in sorted order of their IDs. Unfortunately, you do not have direct access to the evidence room; the only one who has access is Randy, who is corrupt and wants to make things hard for you. In the following we assume that x is the file ID you are looking for.
1. You know that the evidence room is organized as a sorted list of n elements. If Randy was not corrupt you would probably do binary search by asking him to give you the median file of the list. Unfortunately, you can only give Randy two indices l, u and he returns to you a file with index chosen uniformly at random from the range {l, . . . , u}. That is you can call
RANDY(l, u) = (i, ai), where i is a uniformly random integer chosen from l, . . . , u inclusive and ai is the ID of the corresponding file.
You solve the problem by doing something similar to binary search. You start by calling RANDY(1, n). Let’s assume that Randy returns (i, ai). You compare x to ai .
a. If x = ai you found the file you were looking for.
b. If x < ai you call RANDY(1, i − 1)
c. If x > ai you call RANDY(i + 1, n).
You continue recursively until you have either found the file or conclude that the file is not present in the evidence room. Show that the above algorithm accesses O(log n) files in expectation before it terminates.
2. With his trick in the previous question Randy was not able to slow you down very much1 . Now he decides to disallow "range" queries as above and only allows either sequential access to the files or access to a uniformly random file from the entire set. In particular, you now have two ways of accessing the list:
a. By looking at a uniformly random element of the list. That is by calling RANDY() = ai , where i is chosen uniformly at random from 1, . . . , n, inclusive.
Observe that you only receive the file ID, not the index of the file.
b. By asking Randy to give you the file directly following one he returned to you in some previous call. For example if you first call RANDY() and get back ai you are allowed to call NEXT(ai) and get back ai+1. Note that the list wraps around, so that NEXT(an) returns a1. If you haven’t already obtained ai in some previous call you may not call NEXT(ai).
To facilitate analyzing this setting, think of the files as being organized in the form of a circular sorted linked list where every file points to the one with the next higher ID.
(a) As a warm up, let us analyze the following setting. You are given a circle of unit circumference. You pick k points on the circle independently and uniformly at random and snip the circle at those points, obtaining k different arcs. Determine the expected length of any single arc. (Hint: Note that the length of each arc is identically distributed, so each has the same expectation. What is the sum of their expectations?)
(b) Develop a randomized algorithm for finding the file with ID x that makes at most O( √ n) calls to the functions NEXT() and RANDY() in expectation and always returns the correct answer. Analyze the running time of the algorithm. A proof of correctness is not necessary. (Hint: Your algorithm will perform some random accesses and some amount of linear search. Use part (a) to analyze the number of steps in the linear search)

Answers: 2
Another question on Computers and Technology

Computers and Technology, 23.06.2019 07:30
What part of the interface displays the external references contained in a selected cell? the status bar the review tab the scroll bar the formula bar
Answers: 1

Computers and Technology, 24.06.2019 07:00
Into what form does the barcode reader convert individual bar patterns?
Answers: 1

Computers and Technology, 24.06.2019 15:30
What is the total number of time zones that can be configured to show by default in a calendar in outlook 2016?
Answers: 1

Computers and Technology, 25.06.2019 08:20
With technology, information is sent to users based on their previous inquiries, interests, or specifications.
Answers: 2
You know the right answer?
You are a police officer trying to crack a case. You want to check whether an important file is in t...
Questions


History, 05.05.2020 04:02

Mathematics, 05.05.2020 04:02




Spanish, 05.05.2020 04:02

Mathematics, 05.05.2020 04:02


Mathematics, 05.05.2020 04:02



Mathematics, 05.05.2020 04:02


Mathematics, 05.05.2020 04:02


Mathematics, 05.05.2020 04:02



Mathematics, 05.05.2020 04:02