Computers and Technology, 20.04.2020 01:45 XAINEE
Assume that the classes listed in the Java Quick Reference have been imported where appropriate.
Unless otherwise noted in the question, assume that parameters in method calls are not null and that methods are called only when their preconditions are satisfied.
In writing solutions for each question, you may use any of the accessible methods that are listed in classes defined in that question. Writing significant amounts of code that can be replaced by a call to one of these methods will not receive full credit.
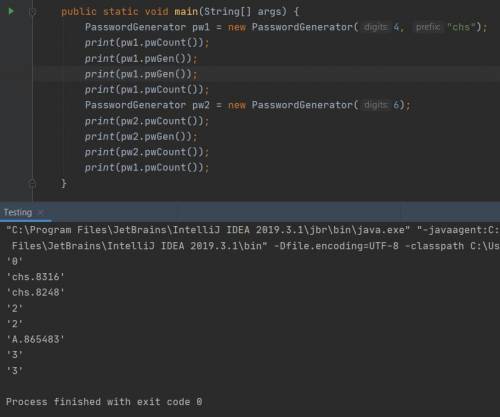
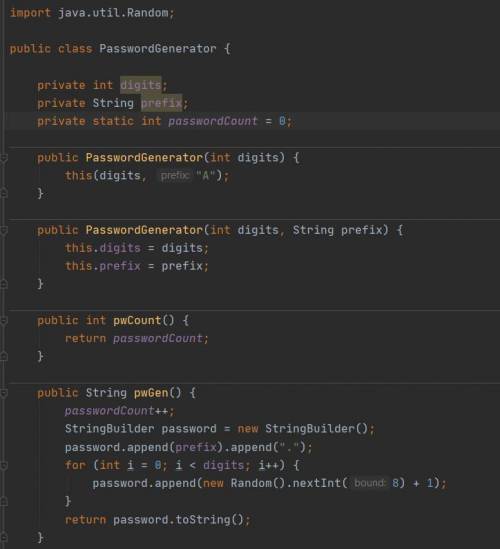
This question involves the implementation of the PasswordGenerator class, which generates strings containing initial passwords for online accounts. The PasswordGenerator class supports the following functions.
Creating a password consisting of a specified prefix, a period, and a randomly generated numeric portion of specified length
Creating a password consisting of the default prefix "A", a period, and a randomly generated numeric portion of specified length
Reporting how many passwords have been generated
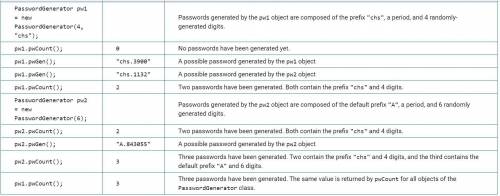
The following table contains a sample code execution sequence and the corresponding results.
The same value is returned by pwCount for all objects of the PasswordGenerator class.
Write the complete PasswordGenerator class. Your implementation must meet all specifications and conform to the example.

Answers: 1
Another question on Computers and Technology

Computers and Technology, 24.06.2019 00:40
Use a software program or a graphing utility with matrix capabilities to solve the system of linear equations using an inverse matrix. x1 + 2x2 − x3 + 3x4 − x5 = 6 x1 − 3x2 + x3 + 2x4 − x5 = −6 2x1 + x2 + x3 − 3x4 + x5 = 3 x1 − x2 + 2x3 + x4 − x5 = −3 2x1 + x2 − x3 + 2x4 + x5 = 5
Answers: 3

Computers and Technology, 25.06.2019 01:30
Once a vulnerability has been identified by nessus, where would you check for more information regarding the identified vulnerability, exploits, and any risk mitigation solution?
Answers: 1

Computers and Technology, 25.06.2019 12:30
What is the purpose of lookup tables in spreadsheet software
Answers: 1

Computers and Technology, 25.06.2019 16:00
Which phrases/sentences correctly state the goals of business information management? multiple choice. john is a business information management professional in new york city. his job (includes regular travel). john has to (analyze business needs) regularly. a few months ago, john had to (manage work schedules in three projects at a time). however, his experience in information management him to manage each project effectively. he was also able to (analyze problems and implement possible business solutions). additionally, john was able to (achieve the corporate goals and manage business knowledge).
Answers: 1
You know the right answer?
Assume that the classes listed in the Java Quick Reference have been imported where appropriate.
Questions



Mathematics, 03.12.2019 07:31

English, 03.12.2019 07:31




Geography, 03.12.2019 07:31

Social Studies, 03.12.2019 07:31




English, 03.12.2019 07:31


Mathematics, 03.12.2019 07:31

Mathematics, 03.12.2019 07:31



Mathematics, 03.12.2019 07:31

Social Studies, 03.12.2019 07:31