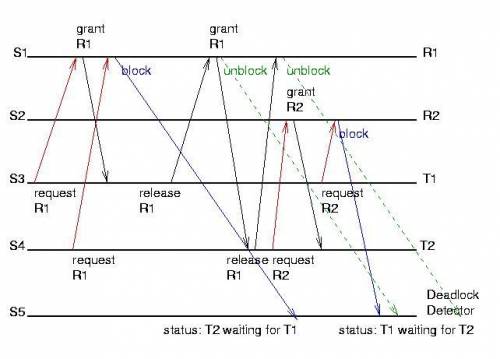
Given the following scheme for distributed deadlock detection:
Processes are assigned un...

Computers and Technology, 05.05.2020 19:20 patriciamelton57
Given the following scheme for distributed deadlock detection:
Processes are assigned unique priorities. When a process waits for an object being locked by another process, deadlock detection is initiated and a probe is sent out to the process where the object is locked. When a probe arrives at an unblocked process or a blocked process with priority higher than the probe initiator, the probe is discarded; otherwise the probe is forwarded along the wait-for edge. A deadlock is declared when a probe returns to the site where it is originated.
Given a scenario with 4 processes P0, P1, P2, and P3, and 4 resource types R0, R1, R2, and R3, where each process resides in a separate site and each resource type has a single instance. Currently, each Ri is assigned to Pi, for 0 ≤ i ≤ 3. Processes are prioritized, with P0 being the highest and P3 the lowest.
Suppose at this time, each Pi is requesting for resource R(i+1) mod 4, for 0 ≤ i ≤ 3. (A deadlock cycle should have formed as a result.) These requests will trigger deadlock detection according to the above scheme. Follow the analysis steps below to determine the total number of messages transmitted in detecting this deadlock.
Construct the resource allocation graph of this system.
Convert the resource allocation graph into a corresponding wait-for-graph. Observe the formation of a cycle, which represents the existence of a deadlock.
Find the number of messages transmitted from each probe initiated, and compute the total.
Generalize the above scenario to n processes in n sites, with each process holding a separate resource and requesting for an assigned resource in the same pattern as described above, and determine the total number of messages transmitted for the detection of the existing deadlock.
above represents the worst case performance for the given deadlock detection scheme in terms of the total number of messages transmitted for detecting a deadlock formed under the following conditions: every site is running one process, resource requests by individual processes are limited to one resource at a time, and there is currently a deadlock cycle that involves all n processes. Find the performance of the scheme for a best case scenario with n processes.

Answers: 3
Another question on Computers and Technology

Computers and Technology, 21.06.2019 21:30
What elements related to the release and success of the nes console do you see in modern console releases? what elements are no longer relevant to modern console gaming?
Answers: 3

Computers and Technology, 24.06.2019 07:20
Ingrid started speaking about her slide presentation. when she clicked to th"third slide, which had just a picture of an elephant, she forgot what she wassupposed to talk about. what could ingrid do to avoid this situation in thefuture? oa. print handouts for her audience.ob. add presenter's notes to each slide.oc. add a video to each slide.od. save her slide presentation to a flash drive
Answers: 2

Computers and Technology, 24.06.2019 17:00
Carlos, an algebra teacher, is creating a series of powerpoint presentations to use during class lectures. after writing, formatting, and stylizing the first presentation, he would like to begin writing the next presentation. he plans to insert all-new content, but he wants to have the same formatting and style as in the first one. what would be the most efficient way for carlos to begin creating the new presentation? going under the file tab and opening the first presentation, deleting all content from each page, and adding new content going under the file tab and clicking on new in the left pane, then choosing new from existing going under the design tab and clicking on themes, then selecting the theme that was used for the first template going under the design tab and opening the template that was created for the first presentation
Answers: 2

Computers and Technology, 24.06.2019 18:30
*write a program that defines symbolic names for several string literals (chars between quotes). * use each symbolic name in a variable definition. * use of symbolic to compose the assembly code instruction set can perform vara = (vara - varb) + (varc - vard); ensure that variable is in unsigned integer data type. * you should also further enhance your symbolic logic block to to perform expression by introducing addition substitution rule. vara = (vara+varb) - (varc+vard).
Answers: 1
You know the right answer?
Questions


Mathematics, 15.12.2021 07:00

Biology, 15.12.2021 07:00


Engineering, 15.12.2021 07:00






Mathematics, 15.12.2021 07:00

Mathematics, 15.12.2021 07:00

Mathematics, 15.12.2021 07:00

English, 15.12.2021 07:00


Mathematics, 15.12.2021 07:00

Chemistry, 15.12.2021 07:00

History, 15.12.2021 07:00


Physics, 15.12.2021 07:00