Computers and Technology, 05.09.2020 22:01 liddopiink1
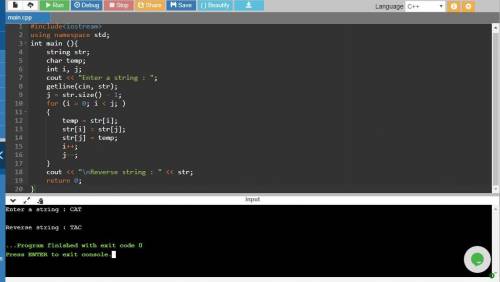
Design a simple algorithm for the string-reverse problem (given a string of characters, your algorithm should return the string with the characters reversed). Example input "CAT" → output "TAC". Don't forget to consider special cases!

Answers: 1
Another question on Computers and Technology

Computers and Technology, 22.06.2019 22:30
One of your customers wants you to build a personal server that he can use in his home. one of his concerns is making sure he has at least one backup of their data stored on the server in the event that a disk fails. you have decided to back up his data using raid. since this server is for personal use only, the customer wants to keep costs down. therefore, he would like to keep the number of drives to a minimum. which of the following raid systems would best meet the customer's specifications? a. raid 0 b. raid 1 c. raid 5 d. raid 10
Answers: 3

Computers and Technology, 23.06.2019 02:30
Rafael needs to add a title row to a table that he has inserted in word. what should he do? use the alignment options. use the merge and center option for all the cells in the top row. use the merge and center option on the first two cells in the top row. none of the above
Answers: 3

Computers and Technology, 24.06.2019 16:30
What is the item which could be matched with a statement below? software installed on a computer that produces pop-up ads using your browser an example of social engineering malware loads itself before the os boot is complete type of spyware that tracks your keystrokes, including passwords windows key + l the practice of tricking people into giving out private information or allowing unsafe programs into the network or computer when someone who is unauthorized follows the employee through a secured entrance to a room or building a type of malware that tricks you into opening it by substituting itself for a legitimate program a computer that has been hacked, and the hacker is using the computer to run repetitive software in the background without the user's knowledge an infestation designed to copy itself repeatedly to memory, on drive space, or on a network
Answers: 1

Computers and Technology, 24.06.2019 22:10
Function name: poly parameters: int returns: int description: a polynomial of degree n with coefficients a0,a1,a2,a3, . . ,an is the function p(x) = a0+a1x+a2x2+a3 ∗ x3+ . . +an ∗ xn this function can be evaluated at different values of x. for example, if: p(x) = 1+2x+ x2, then p(2) = 1+2 ∗ 2+22 = 9. if p(x) = 1+x2+x4, then p(2) = 21 and p(3) = 91. write a function poly() that takes as input a list of coefficients a0, a1, a2, a3, . . , an of a polynomial p(x) and a value x. the function will return poly(x), which is the value of the polynomial when evaluated at x.
Answers: 3
You know the right answer?
Design a simple algorithm for the string-reverse problem (given a string of characters, your algorit...
Questions