Computers and Technology, 29.10.2020 17:10 lailidoll
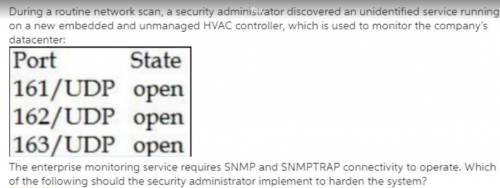
During a routine network scan, a security administrator discovered an unidentified service running on a new embedded and unmanaged HVAC controller, which is used to monitor the company's datacenter:

Answers: 3
Another question on Computers and Technology

Computers and Technology, 22.06.2019 17:30
Working on this program in python 3.7: a year in the modern gregorian calendar consists of 365 days. in reality, the earth takes longer to rotate around the sun. to account for the difference in time, every 4 years, a leap year takes place. a leap year is when a year has 366 days: an extra day, february 29th. the requirements for a given year to be a leap year are: 1) the year must be divisible by 42) if the year is a century year (1700, 1800, the year must be evenly divisible by 400some example leap years are 1600, 1712, and 2016.write a program that takes in a year and determines whether that year is a leap year.ex: if the input is 1712, the output is: 1712 is a leap year. ex: if the input is 1913, the output is: 1913 is not a leap year. your program must define and call the function isleapyear(useryear). the function should return true if the input year is a leap year and false otherwise.
Answers: 1

Computers and Technology, 24.06.2019 09:10
to change the number of rows and columns displayed by the excel object a. select the object and drag a size handle on the active object. b. deselect the object and drag a size handle of the object. c. deselect the object and drag a row or column divider of the object. d. select the object and drag a row or column divider on the active object.
Answers: 2

Computers and Technology, 25.06.2019 00:00
He computer component that disperses heat from the microprocessor to the cooling fan is a cooler thermometer heat sink
Answers: 1

Computers and Technology, 25.06.2019 08:00
In designing a management information system (mis), after defining the system's objectives, the next step is to information in a useful formatintegrate the hardware and software componentscollect and analyze datause information for decision making
Answers: 2
You know the right answer?
During a routine network scan, a security administrator discovered an unidentified service running o...
Questions

History, 22.12.2020 01:30

Mathematics, 22.12.2020 01:30


Social Studies, 22.12.2020 01:30

Mathematics, 22.12.2020 01:30


History, 22.12.2020 01:30

Arts, 22.12.2020 01:30


English, 22.12.2020 01:30



Mathematics, 22.12.2020 01:30



Mathematics, 22.12.2020 01:30

History, 22.12.2020 01:30

Geography, 22.12.2020 01:30

English, 22.12.2020 01:30