NEED HELP ASAP
the table and all other info is in pictures
i will literally cash app you if...

Computers and Technology, 03.12.2020 20:50 gilliancarter2202
NEED HELP ASAP
the table and all other info is in pictures
i will literally cash app you if you want
SHOW ALL YOUR WORK. REMEMBER THAT PROGRAM SEGMENTS ARE TO BE WRITTEN IN JAVA
Assume that the classes listed in the Java Quick Reference have been imported where appropriate.
Unless otherwise noted in the question, assume that parameters in method calls are not null and that methods are called only when their preconditions are satisfied.
In writing solutions for each question, you may use any of the accessible methods that are listed in classes defined in that question. Writing significant amounts of code that can be replaced by a call to one of these
methods will not receive full credit
This question involves a simulation of a two-player game. In the game, two simulated players each start out with an equal number of coins. In each round, each player chooses to spend either 1, 2 or 3 coins. Coins are
then awarded to each player according to the following rules.
Same rule: If both players spend the same number of coins, player 2 gains 1 coin
Off-by-one rule: If the players do not spend the same number of coins and the positive difference between the number of coins spent by the two players is 1. player 2 is awarded 1 coin
Off-by two rule: If the players do not spend the same number of coins and the positive difference between the number of coins spent by the two players is 2. player 1 is awarded 2 coins.
The following is an example of a game played with a starting value of 10 coins and a game length of 5 rounds.
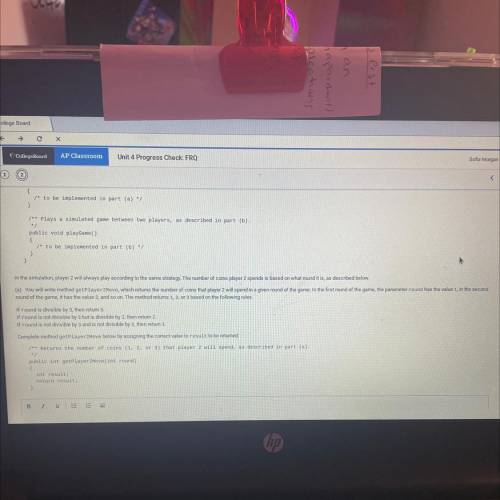

Answers: 1
Another question on Computers and Technology

Computers and Technology, 22.06.2019 12:50
You have just been hired as an information security engineer for a large, multi-international corporation. unfortunately, your company has suffered multiple security breaches that have threatened customers' trust in the fact that their confidential data and financial assets are private and secured. credit-card information was compromised by an attack that infiltrated the network through a vulnerable wireless connection within the organization. the other breach was an inside job where personal data was stolen because of weak access-control policies within the organization that allowed an unauthorized individual access to valuable data. your job is to develop a risk-management policy that addresses the two security breaches and how to mitigate these risks.requirementswrite a brief description of the case study. it requires two to three pages, based upon the apa style of writing. use transition words; a thesis statement; an introduction, body, and conclusion; and a reference page with at least two references. use a double-spaced, arial font, size 12.
Answers: 1

Computers and Technology, 22.06.2019 17:40
Consider the simple 3-station assembly line illustrated below, where the 2 machines at station 1 are parallel, i.e., the product only needs to go through one of the 2 machines before proceeding to station 2.what is the throughput time of this process?
Answers: 2

Computers and Technology, 23.06.2019 03:30
In vista and windows 7, the appearance and personalization option allows you to change the
Answers: 1

Computers and Technology, 23.06.2019 07:00
Why is investing in a mutual fund less risky than investing in a particular company's stock? a. mutual funds only invest in blue-chip stocks. b. investments in mutual funds are more liquid. c. mutual funds hold a diversified portfolio of stocks. d. investments in mutual funds offer a higher rate of return.
Answers: 2
You know the right answer?
Questions

Biology, 03.08.2019 06:30


Business, 03.08.2019 06:30



Biology, 03.08.2019 06:30



Geography, 03.08.2019 06:30


Geography, 03.08.2019 06:30






Mathematics, 03.08.2019 06:30


Mathematics, 03.08.2019 06:30



