
Computers and Technology, 21.01.2021 19:20 seasmarie75
Which of the following scenarios describes an IT professional using good methods to protect passwords and system access of users? Check all of the boxes that apply.
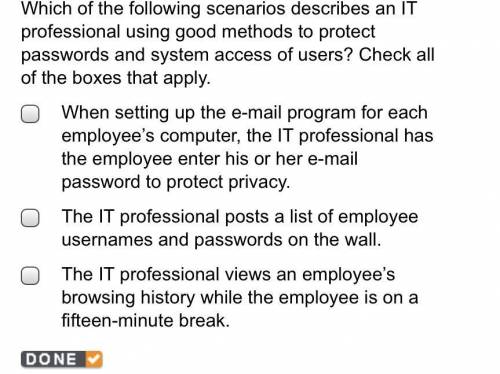

Answers: 1
Another question on Computers and Technology

Computers and Technology, 22.06.2019 03:50
You are working as a security analyst in a company xyz that owns the whole subnet range of 23.0.0.0/8 and 192.168.0.0/8. while monitoring the data, you find a high number of outbound connections. you see that ip's owned by xyz (internal) and private ip's are communicating to a single public ip. therefore, the internal ip's are sending data to the public ip. after further analysis, you find out that this public ip is a blacklisted ip, and the internal communicating devices are compromised. what kind of attack does the above scenario depict?
Answers: 3

Computers and Technology, 22.06.2019 10:00
Businesses allocate resources for their best and most productive uses. the more a resource, the more costly it will be. a manufacturer that requires scarce and costly resources is likely to charge for its products.
Answers: 2

Computers and Technology, 23.06.2019 07:00
You need a quick answer from a coworker. the most effective way to reach your coworker is through a. cloud server b. instant message c. teleconference d. telepresence
Answers: 1

Computers and Technology, 23.06.2019 14:30
Choose the answers that best complete each sentence. on average,are more expensive than other kinds of postsecondary schools. the cost of room and board includes. to save money, some students attend auniversity in their home state.
Answers: 2
You know the right answer?
Which of the following scenarios describes an IT professional using good methods to protect password...
Questions

History, 13.10.2019 01:10



Mathematics, 13.10.2019 01:10

History, 13.10.2019 01:10



Advanced Placement (AP), 13.10.2019 01:10


History, 13.10.2019 01:10







Mathematics, 13.10.2019 01:10

English, 13.10.2019 01:10

English, 13.10.2019 01:10



