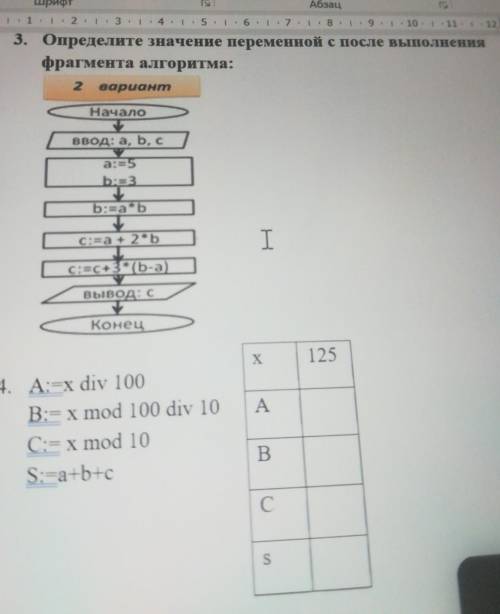
Помогите с информатикой! Срочно!
...

Answers: 3
Another question on Computers and Technology

Computers and Technology, 22.06.2019 07:30
What type of computer network ensures high security ?
Answers: 1

Computers and Technology, 23.06.2019 11:30
Auser is given read permission to a file stored on an ntfs-formatted volume. the file is then copied to a folder on the same ntfs-formatted volume where the user has been given full control permission for that folder. when the user logs on to the computer holding the file and accesses its new location via a drive letter, what is the user's effective permission to the file? a. read b. full control c. no access d. modify e. none of the above
Answers: 1

Computers and Technology, 23.06.2019 19:40
Use a physical stopwatch to record the length of time it takes to run the program. calculate the difference obtained by calls to the method system.currenttimemillis() just before the start of the algorithm and just after the end of the algorithm. calculate the difference obtained by calls to the method system.currenttimemillis() at the start of the program and at the end of the program so that the elapsed time includes the display of the result. use the value returned by the method system.currenttimemillis() just after the end of the algorithm as the elapsed time.
Answers: 3

Computers and Technology, 24.06.2019 14:30
Ahousehold consists of a married couple and their twin five-year old daughters. the couples children had no income and lived with their parents all of last year. how many exemptions can the couple claim on last years tax return or they file with the “ married filing jointly “ status? a. 4 b. 5 c. 3 d. 2
Answers: 1
You know the right answer?
Questions








History, 20.11.2019 02:31


Mathematics, 20.11.2019 02:31

History, 20.11.2019 02:31






History, 20.11.2019 02:31


History, 20.11.2019 02:31

English, 20.11.2019 02:31