
Computers and Technology, 24.02.2021 19:50 janyiareese12
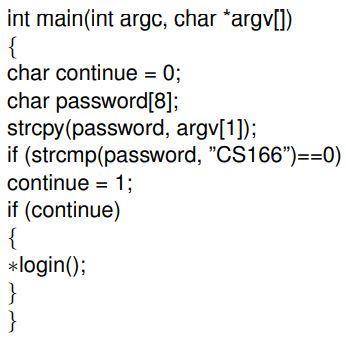
Consider the following piece of C code (in attachment):
In the above code, ∗login() is a pointer to the function login()
(In C, one can declare pointers to functions which means that the
call to the function is actually a memory address that indicates
where the executable code of the function lies). (1) Is this
code vulnerable to a buffer-overflow attack with reference to the
variables password[] and continue? If yes, describe how an attacker
can achieve this and give an ideal ordering of the memory cells
(assume that the memory addresses increase from left to right)
that correspond the variables password[] and continue of the code
so that this attack can be avoided. (2) To fix the problem, a security
expert suggests to remove the variable continue and simply use
the comparison for login. Does this fix the vulnerability? What
kind of new buffer overflow attack can be achieved in a multiuser
system where the login() function is shared by a lot of users (both
malicious and and nonmalicious) and many users can try to log
in at the same time? Assume for this question only (regardless
of real systems’ behavior) that the pointer is on the stack rather
than in the data segment, or a shared memory segment. (3) What
is the existing vulnerability when login() is not a pointer to the
function code but terminates with a return() command? Note that
the function strcpy does not check an array’s length.

Answers: 3
Another question on Computers and Technology

Computers and Technology, 22.06.2019 18:30
Which of the following is an example of intellectual properly! oa. new version of a novelb. journal of ideasc. pages of a bookood. lines of a poem
Answers: 2

Computers and Technology, 23.06.2019 01:10
Problem 1 - hashing we would like to use initials to locate an individual. for instance, mel should locate the person mark e. lehr. note: this is all upper case. generate a hash function for the above using the numbers on your telephone. you know, each letter has a number associated with it, so examine your telephone keypad. generate 512 random 3 letter initials and take statistics on a linked list array size 512 to hold this information report how many have no elements, 1 element, 2 elements, does this agree with the hashing statistics distribution?
Answers: 1

Computers and Technology, 23.06.2019 04:40
The narrative structure of the popular movies can be broken down into
Answers: 3

Computers and Technology, 24.06.2019 03:00
With editing, word automatically displays a paste options button near the pasted or moved text. a. cut-and-paste b. drag-and-drop c. inline d. copy-and-carry
Answers: 1
You know the right answer?
Consider the following piece of C code (in attachment):
In the above code, ∗login() is a pointer to...
Questions


Mathematics, 11.12.2020 09:20

Mathematics, 11.12.2020 09:20

Mathematics, 11.12.2020 09:20

Mathematics, 11.12.2020 09:20

Mathematics, 11.12.2020 09:20

Chemistry, 11.12.2020 09:20

Mathematics, 11.12.2020 09:20

Mathematics, 11.12.2020 09:20

English, 11.12.2020 09:20



Geography, 11.12.2020 09:20









